A Guide To Setting Up Secure Remote Workstations

Remote work has become the new standard for many businesses, offering flexibility and increased productivity. While beneficial, this shift also introduces significant security challenges. Without proper precautions, sensitive data can be at risk, and operations can be disrupted.
Establishing secure remote workstations is essential for protecting your company’s information and maintaining seamless functionality. Implementing robust security measures safeguards data and supports a more resilient and efficient remote working environment.
Read on to discover comprehensive strategies for securing remote workstations that will keep your business safe and productive.
Evaluating Your Remote Workstation Needs
Evaluating your specific requirements is crucial before implementing security measures for your remote workstations. This initial assessment helps ensure that your chosen security setup effectively addresses your vulnerabilities and protects your data.
Here are the factors to consider when evaluating your remote workstation needs:
- Type of work: The nature of the tasks your employees perform remotely significantly impacts the security measures you need. For instance, if employees handle sensitive financial data, you’ll need stricter protocols than a team working on social media content.
- Number of users: The number of remote workers you have will influence the resources required. Scaling your security measures to accommodate a growing remote team is essential.
- Security requirements: Assess the level of sensitivity of the data your employees handle. The more sensitive the data, the more robust your security protocols need to be.
By carefully considering these factors, you create a remote work environment that is both secure and efficient. Many financial institutions like Credibly based in USA can offer guidance and resources to help small businesses invest in the necessary tools and technologies to secure their remote workstations.
Securing Network Connections
Secure network connections are the bedrock of a safe remote work environment. They act as a digital barrier, safeguarding sensitive data as it travels between remote workstations and company servers.
Here’s how to fortify your network defenses:

- Utilize virtual private networks (VPNs): VPNs encrypt internet traffic, creating a secure tunnel between remote devices and your internal network. This encryption scrambles data, which makes it unreadable to anyone snooping on the connection.
- Implement firewalls: Think of firewalls as security guards for your network. They meticulously examine incoming and outgoing traffic, allowing only authorized data to pass through. Firewalls effectively block unauthorized access attempts, helping to prevent malware infiltration and data breaches.
- Maintain up-to-date software: Outdated software often contains vulnerabilities that cybercriminals can exploit. By religiously applying updates for your operating systems, network applications, and web browsers, you ensure these vulnerabilities are patched, and your network remains protected.
Establishing robust network security lays the groundwork for a safe and reliable remote work ecosystem.
Training Employees On Security Best Practices
An empowered workforce is a secure workforce. Equipping your team members with the knowledge to identify and combat security threats is paramount in protecting your remote work environment. Partnering with IT support services, like those offered by Salt Lake City IT support firms, can provide valuable technical expertise, and educating your team fosters a culture of cybersecurity awareness.
Here are some topics to cover in your employee security training:

- Phishing awareness: Train your employees to recognize the hallmarks of phishing scams. This includes suspicious emails, urgency tactics, and requests for personal information. Teach them to verify sender legitimacy, avoid clicking on unknown links, and report suspected phishing attempts.
- Secure communication: Employees should understand the importance of using secure communication channels. This may involve using company-approved messaging platforms and avoiding public Wi-Fi for sensitive data transmission.
- Password hygiene: Strong passwords are crucial; they’re the first line of defense against unauthorized access. So, train your employees on creating complex combinations of lowercase and uppercase and letters, symbols, and numbers. Equally important is emphasizing the importance of never sharing passwords and changing them regularly.
- Incident reporting: Establish a clear protocol for employees to report security incidents promptly. This could include suspicious activity, malware infections, or lost devices. Timely reporting allows for faster mitigation and reduces potential damage.
Investing in employee security training will equip your team with the right information and skills to become active participants in safeguarding your remote work environment.
Implementing Strong Authentication Methods
In today’s digital landscape, passwords alone are no longer sufficient to safeguard remote access. By fortifying your defenses with robust authentication methods, you introduce another layer of security, significantly detering unauthorized access attempts to sensitive information.
Here are some methods to consider:
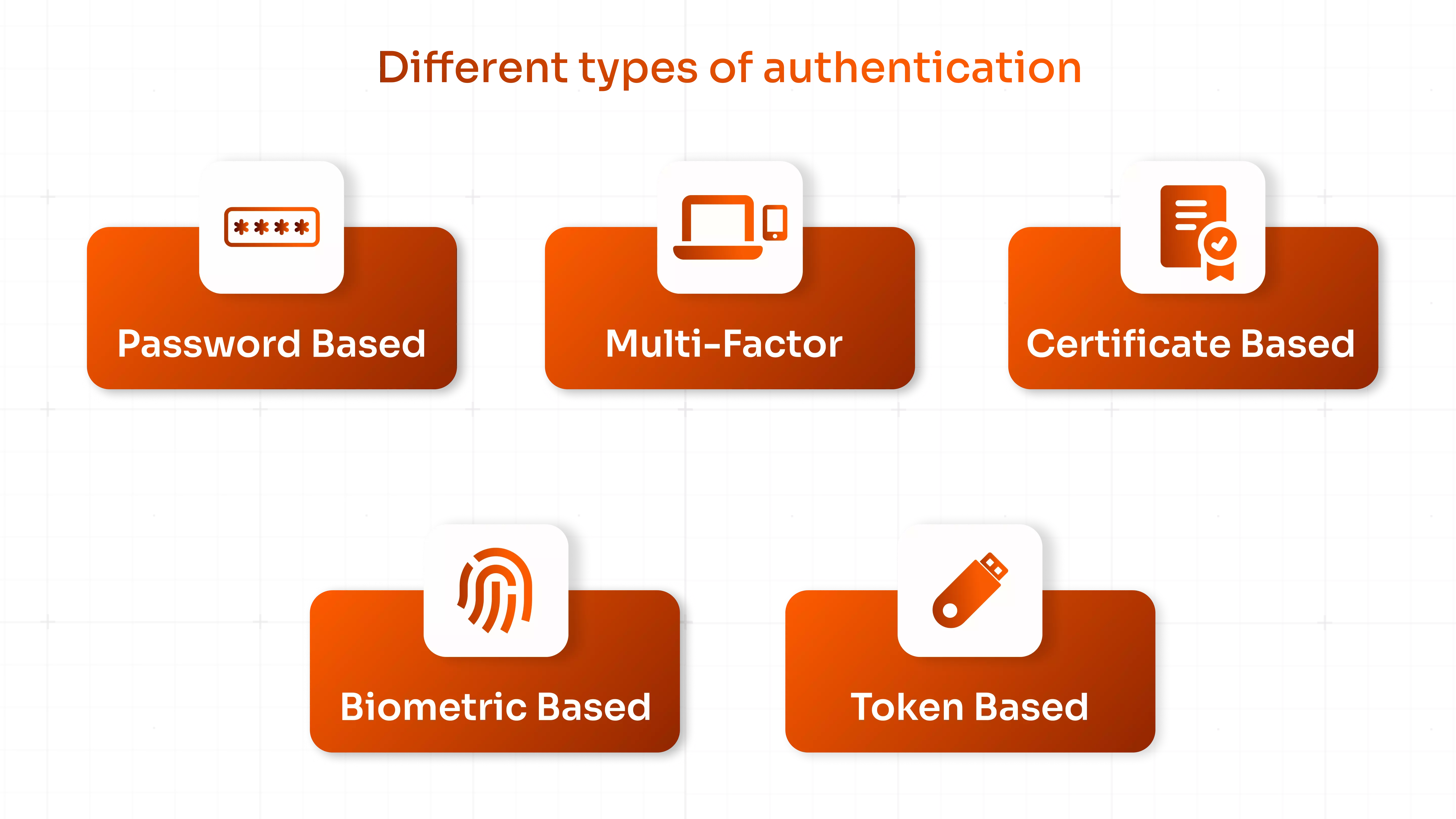
- Multi-factor authentication (MFA): MFA goes beyond traditional passwords, requiring users to provide additional verification factors during login. This could involve a code sent to a trusted device, fingerprint or facial recognition. So, even if a password is compromised, unauthorized access becomes significantly more difficult.
- Single sign-on (SSO): While strong passwords are essential, managing multiple login credentials can be cumbersome. SSO simplifies the login process by allowing users to access various applications with single credentials. This reduces password fatigue and the temptation to reuse weak passwords across different platforms.
- Password policies: Enforce strong password policies to bolster your first line of defense. These policies should mandate a minimum password length, character variation (including uppercase, lowercase, symbols, and numbers), and regular password changes. Educating employees on proper password hygiene is also crucial to the effectiveness of password policies.
Implementing a combination of these authentication methods enhances your remote workstation security posture.
Protecting Devices With Endpoint Security
Remote workstations act as the frontline for accessing company data. Since these devices are often used outside the controlled environment of a physical office, endpoint security becomes paramount.
Here are essential measures to safeguard your remote devices:
- Install antivirus and anti-malware software: Antivirus and anti-malware software act as the first line of defense against malicious software. These programs proactively scan for and neutralize viruses, malware, and other cyber threats that can steal data or disrupt operations.
- Enable device encryption: Data encryption scrambles information on a device, rendering it unreadable without a decryption key. Encryption significantly reduces data breaches risks in the event of a lost or stolen device.
- Implement mobile device management (MDM) for company-issued devices: MDM solutions provide centralized management of smartphones, tablets, and laptops. They allow IT administrators to configure security settings, enforce policies, and remotely wipe data from lost or stolen devices.
- Educate employees on safe remote work practices: Educate your employees on potential security risks associated with using remote devices. This includes training them to identify phishing attempts, avoid using public Wi-Fi for sensitive and work-related tasks, and report any suspicious activity.
By implementing a comprehensive endpoint security strategy, you can significantly bolster the defenses of your remote workstations and safeguard sensitive data.
Ensuring Secure Access To Company Resources
Granting access to company resources in a remote work environment requires a delicate balance. While employees need access to perform their jobs effectively, minimizing exposure to sensitive data is crucial.
Here are key strategies to implement:
- Implement role-based access control (RBAC): RBAC grants permissions according to an employee’s job role. This ensures team members can only access data and resources needed to perform their tasks. For instance, a marketing team member couldn’t access financial data.
- Use secure file-sharing solutions: With the rise of cloud technology, cloud storage has become commonplace, but security is paramount. Utilize file-sharing platforms that offer encryption to safeguard data at rest and in transit.
- Monitor access logs: Review access logs regularly to track user activity and identify suspicious patterns. This can help detect unauthorized access attempts or potential insider threats.
- Enforce the principle of least privilege: Implementing the principle of least privilege means that users should have only the necessary access levels for their roles. This approach minimizes the potential harm from unauthorized access.
Effectively managing access controls helps safeguard sensitive data and lowers the attack surface for cyber threats.
Regularly Updating And Patching Systems
Cybercriminals constantly discover and exploit software vulnerabilities. Implementing a regular system update and patching regime is key to staying ahead of these threats.
Here are some practices to ensure your systems remain current and secure:
- Automate updates: Whenever possible, automate software updates and patch installations. This proactive approach ensures timely vulnerability fixes, minimizing the window attackers can exploit.
- Schedule regular maintenance windows: Plan regular maintenance windows to apply updates that require system restarts. This minimizes disruption to workflow and ensures critical updates are not delayed.
- Monitor for vulnerabilities: Proactively monitor for new vulnerabilities and threats. Many security vendors offer vulnerability scanning tools and advisories to keep you informed.
- Prioritize updates: Prioritize applying critical security patches as soon as they become available. These patches address the most recently discovered and high-risk vulnerabilities.
By staying current with updates and patches, you’ll be proactive in reducing the attack surface for cyber threats and bolster the overall security posture of your remote workstations.
Backing Up Data Securely
Data loss can be devastating, especially in a remote work environment. Regular data backups are essential for recovering from cyberattacks, hardware failures, or accidental deletion.
Here are some practices to ensure your backups are secure and reliable:
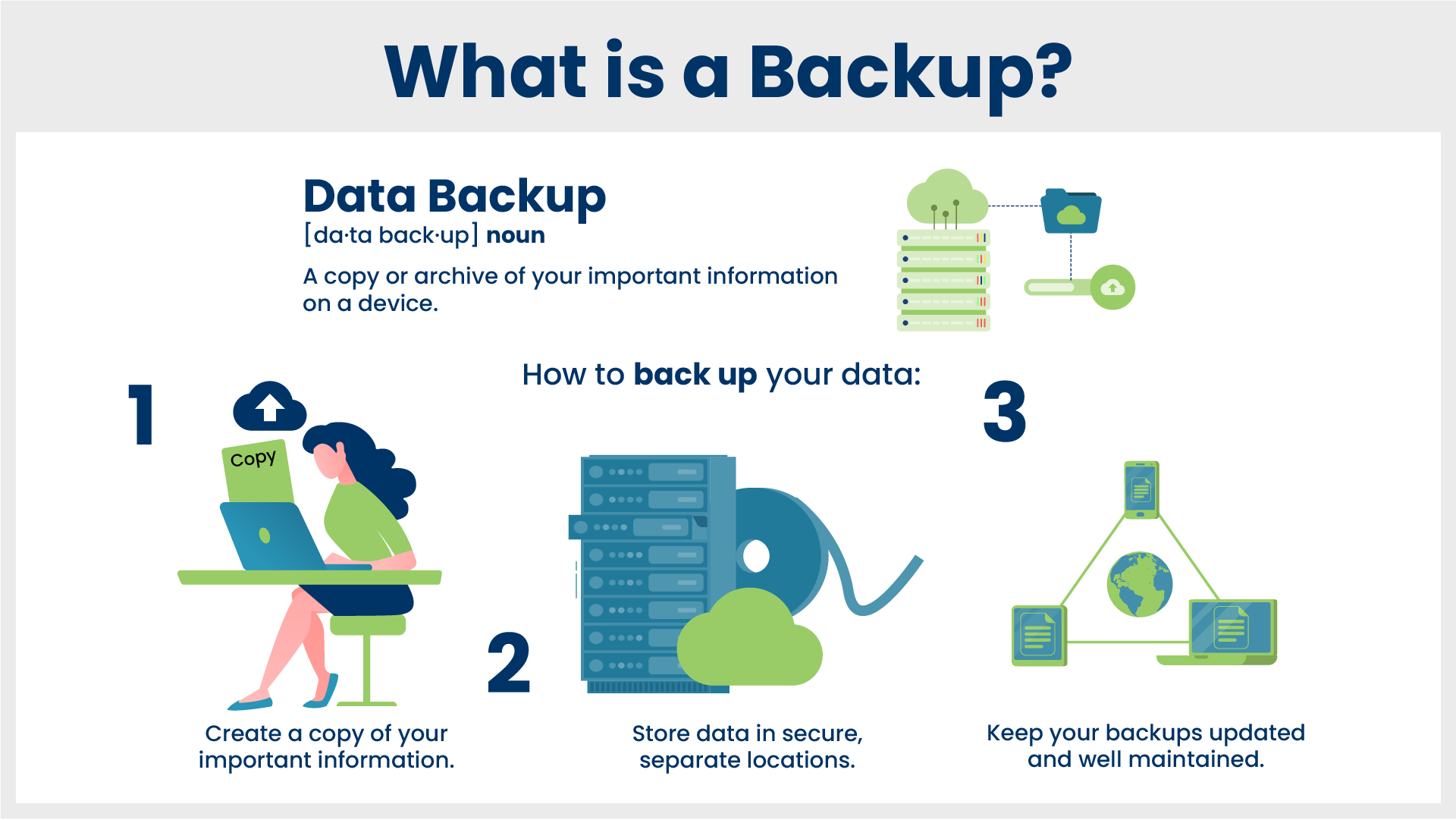
- Use encrypted backups: Encryption scrambles your data, rendering it unreadable without a decryption key. This adds an extra layer of defense in case your backups are compromised.
- Store backups offsite: Don’t store backups on the same devices or network as your primary data. Consider cloud or physical backups stored in a separate location to protect against physical disasters like fires or floods.
- Test backup recovery: Regularly test your backup recovery process to ensure it functions as intended. This helps identify any issues before a critical data loss event.
By implementing a secure data backup strategy, you can ensure business continuity and reduce downtime during a disruption.
Conclusion
Securing remote workstations is vital for protecting sensitive data and ensuring smooth operations. You create a resilient remote work environment by evaluating your workstation needs, securing network connections, implementing strong authentication methods, and protecting devices with endpoint security.
Additionally, ensuring secure access to resources, regularly updating systems, and backing up data securely fortifies your defenses. Investing in training your team members on security best practices further enhances your company’s overall security posture. By following these comprehensive strategies, your business can confidently embrace remote work while safeguarding its critical assets.

